Choosing Credentials and Card Technology
Card technology has evolved dramatically in the past 25 years, as has the application of the technology in the access control card industry and the ability to fraudulently copy or clone a card.
While there may be little visible difference between an old 125kHz proximity card and a 13.56MHz smart card - you present the card at a reader and access is either granted or denied - what happens behind the scenes is quite different. Apart from the frequency that is used to transmit data, there are significant differences between the technologies, particularly when it comes to the level of security.
Understanding these differences is important in ensuring the solution you implement doesn’t put your business at risk.
In all cases you should be looking to implement a minimum of MIFARE DESFire EV1 technology. Where this is not possible, consider adding a second level of authentication that requires a user to present both a card and a PIN or biometric credentials.
Card Technology Security Comparison
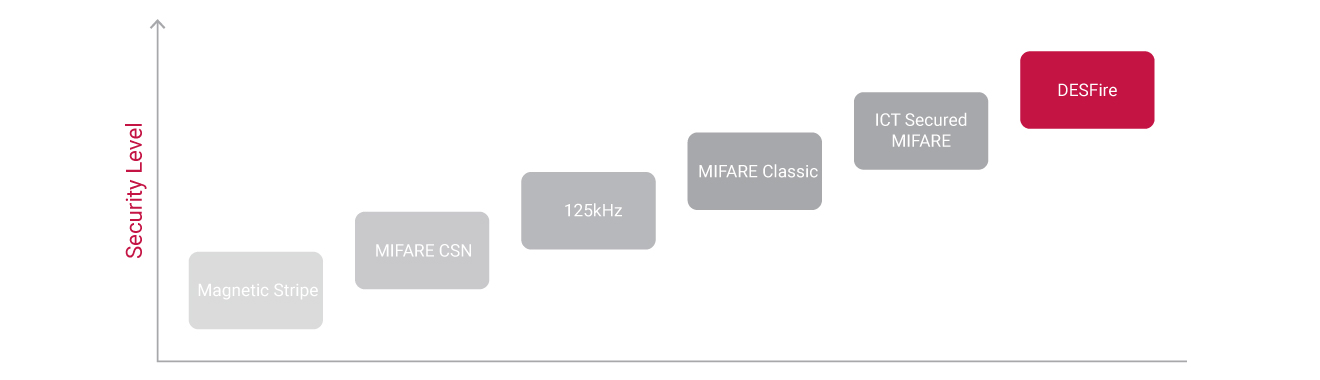
Historically, card-based access control systems were built around a card with a magnetic stripe. These cards required a user to swipe the card through a magnetic reader to gain access to a door. This technology had a number of disadvantages, including an inconvenience factor, a high wear rate, and very low security. It was these disadvantages that led to the development of contactless proximity technology, allowing cards to be read without making physical contact with the reader.
Proximity readers work by constantly emitting a short range radio frequency (RF) field. When a proximity card comes within range of this field, an integrated chip within the card is powered up and the chip transmits a card number back to the reader. Not all proximity cards are born equal though, and it is important that the differences are weighed up when making a decision about which technology to adopt.

125kHz (Proximity)
The first of the proximity technologies was 125kHz. When a 125kHz card comes within range of a reader, the card immediately begins to transmit its card number. The data transmitted by the card is not encrypted and is always the same. Data transfer is only one way. In effect, this is very similar to the way the old mag-stripe readers worked.
Apart from being low cost, the only real advantage of 125kHz is that due to the lower power requirements and small amount of data being transmitted, it offers a good read range (of around 10cm or 3.9in) and a short read time. This allows users to present, swipe, or wave their card in the general direction of the reader to get a successful read.
The key disadvantage however, is the low level of security. The ability to copy 125kHz cards - commonly referred to as ‘Prox’ cards - has existed for more than 20 years. Proximity 125kHz copy and emulation circuits have been available to the public for many years, and with instructional videos easy to find and cloning devices readily available on popular shopping websites for less than $30, it’s possible for anyone to copy 125kHz cards today. There are even shop fronts and kiosks that offer card cloning services operating in many cities around the world.
While 125kHz cards are still commonly used, the widely publicized security flaws must be given serious consideration.
13.56MHz (Smartcard)
The 13.56MHz MIFARE standard was originally created as a ticketing solution for transport systems, while also addressing the security issues with 125kHz technology by enabling two way communication between the card and reader. This saw the introduction of card encryption and the ability to store data on the card.
Most MIFARE technologies store the card number in one of the storage areas on the card, known as sectors. When the card approaches the RF field of the reader, the card and reader begin a secure communication session using shared encryption keys. Once this is established, the card number is transmitted and the communication session is closed off. This process happens very quickly, however it does take slightly longer than a 125kHz based system and means that generally, a MIFARE card cannot be simply swiped or waved at a card reader, but must be presented. Also, the two way process requires more energy than 125kHz, meaning a slightly reduced read range of around 7cm (2.7in).
Along with the added security, the additional storage space on the card can be used for many applications, such as offline locking systems or the storage of credit for pay as you go systems.
MIFARE comes in many forms, each with their own advantages and disadvantages.

Comparing MIFARE Technologies
Site Codes and Custom Encryption Keys
Site Codes
Each card is made up of a site code and a card number. The site code is designed to be unique to a particular site or building, meaning that a card from one building would not allow access at another building, even if the card number was the same.
With 125kHz, there are so many producers of cards world-wide and a relatively small number of site codes available, that it is possible - or even likely - that many legitimate versions of the same card exist. To make matters worse, some installers will simply label a customer as Site 1 and then add Card 1, Card 2, Card 3, Card 4, and so on. If there’s no deliberate attempt to increase the complexity of a customer’s numerical base, there can be many duplications locally and globally.
On the other hand, when ordering ICT Secured MIFARE and MIFARE DESFire cards, every site is registered with its own globally unique site code, and every card produced is recorded in ICT’s secure database. This ensures we never create duplicate cards. These cards are further protected with a layer of encryption using ICT’s diversified authentication key.
Custom encryption keys
ICT also provides the ability for an integrator or end user to purchase their own reserved set of encryption keys. This effectively gives the organization their own entire set of globally unique site codes and card numbers, protected with their unique encryption key, for that site. This means there is no chance of other cards (from ICT or other vendors) from ever working on that site.
The integrator or end user can also choose to encode their own cards at their site as and when they require them. This is still a managed system, ensuring that duplicates cannot be made.

Transitioning from 125kHz Proximity to 13.56MHz MIFARE DESFire
Migrating from legacy systems that use insecure, low frequency 125kHz cards and readers may seem daunting - but it doesn’t need to be. A progressive upgrade can be performed using either dual technology cards or multi technology readers which allows you to transition to smart technology at your own pace.
Dual technology cards incorporate both high and low frequency card inlays enabling readers to be changed one by one. These cards only need to be issued to users requiring access to doors with upgraded readers. For example, readers controlling access to high-security rooms (such as a server room) could be upgraded to DESFire card technology. Staff requiring access to the server room would need dual technology cards, allowing them access to both the low-security 125kHz-technology doors and the high-security DESFire-secured doors. Remaining staff can continue to use their old cards until other readers are upgraded.
ICT’s multi technology tSec readers combine both 125kHz and 13.56MHz capabilities in a single unit so you don't need to replace all cards upfront. This allows for the gradual replacement of users' cards. Once all users have new cards, the low-security 125kHz card option can be disabled at the reader. This can also be a good option for common areas of a multi-tenanted building, allowing tenants to choose either technology for their own fitout.

Other Credential Options
PIN codes
While they are durable, low-maintenance, and easy-to-use, PIN codes aren’t immune to security flaws. Employees can easily share their access code with an unauthorized user and it is also possible for an unauthorized user to witness the combination code as it is being entered by a legitimate user. PIN codes are ideal when implementing a second level of authentication however we wouldn’t recommend using them as the primary means to access a building.
Mobile credentials
Compared to traditional cards and tags, mobile credentials offer a more convenient end user experience by leveraging a device the user already has, meaning lost and forgotten cards become a thing of the past. By eliminating the need for physical cards, you also eliminate the time and effort involved with handling, printing, and distributing them. Ordering, issuing, and managing credentials is all done online, and the credential is emailed directly to the end user’s mobile device.
Credentials are stored securely on the mobile device, with access authenticated using a secure cloud based server and 256-bit encryption. Given that most people carry their smartphone everywhere, just as they do their car-keys and wallet, mobile credentials are much less likely to be lost or misplaced. This significantly reduces issues around being unable to access the building, and in the event that a phone is lost, the owner is usually very quick to notice, ensuring a prompt notification of lost credentials which reduces the security risk. Most devices are also usually protected with a passcode and/or biometrics, further increasing security.
Biometric credentials
Biometric credentials provide access based on who people are – verifying the user based on unique physical characteristics, such as a fingerprint, iris scan, or facial recognition - rather than what they have in their possession.
This certainly increases protection, after all, biometric credentials can’t be forgotten, shared, lost, or stolen. Furthermore, most modern systems are equipped with advanced detection technology that won’t accept anything less than a live biometric identifier, blocking fake credentials such as fingerprints made from silicon, 3D printed masks, and other creative attempts to deceive the system.
While biometrics are secure and convenient, the technology does come at a cost. Biometric readers have a significantly higher price tag than traditional RFID readers, so many organizations opt to only use them to control access to restricted/high-security areas, while using standard card readers for the rest of the site.
Two Factor Authentication
Two factor authentication ensures that the person standing at the door is who they claim to be. It’s designed to prevent unauthorized users from presenting a lost or stolen card or using another users PIN code to unlawfully gain access. It uses a combination of credentials – usually what you have (a physical card or mobile credential), and either what you know (PIN) or who you are (biometric data). Each of these authentication methods have varying levels of security on their own, but when combined, they can offer the high level of security often required by data centers, medical facilities, and financial institutions.
Two factor authentication can be easily implemented at a single door, or across an entire site, using a card reader with an inbuilt PIN pad, or by combining a card reader with a traditional alarm keypad or biometric reader. It can even be enabled at certain times of day or based on other conditions such as whether the system is armed.
Summary
While 125kHz technology is still widely used after nearly three decades, many companies are not aware of the risks of choosing low security card technology. It may seem appealing due to the low price, however it is too easily compromised. MIFARE DESFire provides a much higher level of security as well as greater operational flexibility.
If you want a system that offers any form of serious protection, a MIFARE DESFire solution should be top on your list.

Secure your future
If you’d like to find out more about how your facility can transition to secure smart card technology using a single cohesive and unified solution from ICT, get in touch with your local sales professional.
